According to the 2024 IBM Cost of a Data Breach Report, the average cost of a data breach for businesses with extensive cloud adoption is $4.88 million. That staggering figure highlights a critical dilemma for many small- and mid-sized organizations: the cloud promises better agility, but it also presents unfamiliar cyber pitfalls.
| “Cloud security isn’t just an IT issue—it’s the foundation upon which your entire digital strategy stands.” says Jason Cary, VP of Sales at FTI Services |
If you’re feeling the urgency to shield sensitive data and maintain client trust, you’re not alone. Below, you’ll find strategies to help you stay a step ahead and avoid unnecessary vulnerabilities.
Cloud Security 101
To begin with, what exactly is cloud security? It encompasses the policies, technologies, and controls that safeguard your data, applications, and infrastructure within a cloud environment. If you’re curious about what cloud computing security entails, you’re essentially asking how these protective measures adjust to the shared and on-demand characteristics of the cloud—a curiosity growing more urgent by the day. In fact, according to CloudSecureTech, 87% of companies now rely on cloud services to run core parts of their business.
Unlike traditional on-premises setups, cloud ecosystems often outsource infrastructure, storage, and platform services to third parties. This introduces new complexities: you must assess cloud providers as meticulously as you would your own IT department. That means examining everything from compliance standards (e.g., HIPAA, PCI-DSS) to incident response protocols and day-to-day security practices. Also crucial is understanding the shared responsibility model, which clarifies where a provider’s obligations end and yours begin. The provider typically secures the underlying infrastructure “of” the cloud, while you handle what’s placed “in” the cloud, including data encryption, identity management, and access controls.
For a concise overview of core cloud security definitions, explore this helpful NIST reference (National Institute of Standards and Technology).
Hidden Dangers in the Cloud – Are You Safe?
While cloud adoption continues to skyrocket, many small and mid-sized businesses unknowingly overlook hidden vulnerabilities that can compromise their entire digital ecosystem. A well-protected cloud environment starts with understanding the most significant threats lurking beneath the surface.
- Misconfigurations: An incorrectly set up cloud environment can leave sensitive information publicly accessible. If you aren’t regularly reviewing permissions and settings, you risk exposing confidential data to anyone who stumbles upon it.
- Insider Threats: Not all threats come from hackers. Employees or contractors with elevated privileges can inadvertently (or intentionally) cause major security breaches. Strong access controls and monitoring can mitigate this risk.
- Advanced Persistent Threats (APTs): Cybercriminals often play the long game. They infiltrate a system and remain undetected for extended periods, quietly collecting data or planting malicious software.
- Shared Technology Vulnerabilities: In a multi-tenant cloud environment, a flaw in one organization’s setup can sometimes compromise the broader infrastructure. This underscores the need for rigorous vendor assessments and isolation strategies.
- Weak Credential Management: Simple or repeated passwords, inadequate multi-factor authentication, and outdated login practices can become open invitations to attackers. Ensuring robust authentication protocols is crucial.
- Phishing & Social Engineering Attacks: Unsuspecting employees clicking harmful links can compromise entire cloud systems. Comprehensive training programs and simulated phishing tests help keep your team vigilant.
- Data Loss or Outages: Whether triggered by a cyber incident, hardware failure, or natural disaster, losing access to your data can devastate operations. Regular backups and clear recovery procedures are non-negotiables.
| Further, Explore How Managed IT Services Can Benefit Your Business:
How Managed IT Services Work For Your Business Staff Augmentation vs. Managed IT Services: Making the Right Choice for Your Business |
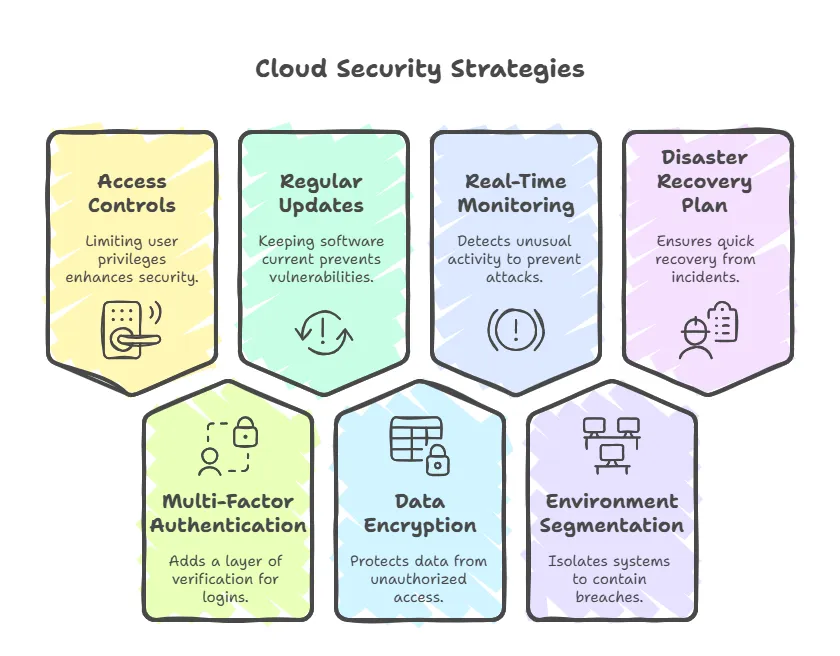
7 Cloud Security Strategies for SMBs That Actually Work
Securing your digital assets isn’t just about following a checklist—it’s about adopting proactive, proven measures that address the unique challenges smaller organizations face. The seven strategies below are designed to reduce risk, enhance resilience, and help you drive cloud operations confidently into the future.
- Enforce Strong Access Controls: Limiting user privileges based on roles ensures that employees only access what they truly need. This prevents an attacker who compromises one account from roaming freely.
- Adopt Multi-Factor Authentication (MFA): Simply requiring a username and password is no longer enough. MFA—via a token, text message, or biometric scan—adds a second layer of verification, drastically reducing unauthorized logins.
- Regularly Patch and Update: Outdated software is a prime target for hackers. Schedule frequent checks and ensure critical systems are promptly patched to close known vulnerabilities.
- Encrypt All Data: Encrypting data at rest and in transit makes stolen information essentially useless to cybercriminals. Seek cloud providers that offer built-in encryption features for easy implementation.
- Implement Real-Time Monitoring: Automated alerts can help you spot unusual spikes in traffic or suspicious user behavior. Swift detection dramatically increases your chances of containing an attack before it spreads.
- Segment Your Cloud Environment: Separating workloads, databases, and applications prevents a breach in one area from compromising everything. Containers or virtual private clouds (VPCs) can make segmentation both powerful and efficient.
- Develop a Disaster Recovery Plan: Even with the best defenses, incidents can still happen. A solid plan that outlines backups, recovery steps, and communication protocols ensures you can bounce back quickly—and maintain client trust.
Actionable Steps: Building a Holistic Cloud Security Roadmap
Prioritising a cohesive, step-by-step security plan can save you headaches—and money—in the long run. Here’s where to begin:
- Assess Current State: Conduct a thorough audit of existing cloud assets and risk exposure.
- Develop Policies & Training: Spell out how data should be handled, stored, and shared. Train everyone regularly.
- Invest in Monitoring: Leverage automated tools to detect unusual behavior. Link real-time alerts to your IT team or provider.
- Adopt Multi-Factor Authentication: Simple passwords won’t cut it. Enforce multiple layers of verification.
- Plan for Incidents: Create a formal response strategy with designated roles. Drill it.
- Regularly Review & Update: Cyber threats evolve. Your plan should, too.
For a deeper dive into building a security roadmap, the Cloud Security Alliance offers whitepapers covering best practices and frameworks.
Key Areas of Cloud Security
| Aspect | Core Focus | Action Step |
| Workload Security | Isolating and protecting apps | Implement container orchestration and real-time monitoring tools |
| Infrastructure Security | Safeguarding foundational layers | Adopt zero-trust architecture with continuous authentication |
| Data Security | Ensuring sensitive info remains private | Encrypt data at rest and in transit, enforce strict access controls |
| Compliance Management | Meeting regulatory standards | Automate compliance checks using specialized services and frameworks |
| Threat Detection | Spotting and mitigating attacks | Use AI-driven tools that alert your team to anomalies |
Let FTI Services Fortify Your Cloud – Before It’s Too Late
A secure cloud environment isn’t a luxury—it’s a business necessity. With rising threats, stricter compliance demands, and growing reliance on digital infrastructure, protecting your cloud assets should be a top priority. The risks are real, but so are the solutions.
At FTI Services, we specialize in delivering tailored cloud security strategies built for small and mid-sized businesses. From workload protection and data encryption to infrastructure hardening and disaster recovery planning—we cover it all.
Don’t wait for a breach to take action.
Contact FTI Services today to schedule your personalized cloud security consultation and take the first step toward total peace of mind.
| Learn More About Our Services Near You: |


